Passive DNS/TLS Guide
Investigating with Passive DNS/TLS
Section titled “Investigating with Passive DNS/TLS”Passive DNS/TLS helps analysts reconstruct historical DNS changes and discover adjacent infrastructure (IPs, nameservers, MX, and certificate subjects) related to a domain. This is useful for understanding hosting moves, provider changes, and relationships between suspicious domains.
As an analyst it’s also helpful in understanding the history of a Domain. How recent is it? What activity has been occurring, are they switching IPs frequently? All of this helps you better understand not only the Domain at this point in time, but its past behavior as well.
What You Can Do
Section titled “What You Can Do”- Timeline analysis: Review A/AAAA, NS, MX, TXT, and CNAME changes over time
- Infrastructure mapping: Identify IPs, nameservers, and TLS subjects historically associated with a domain
- Change detection: Spot significant flips (e.g., NS churn, MX changes)
- Context building: Correlate passive signals with lookup results, rules, and alerts
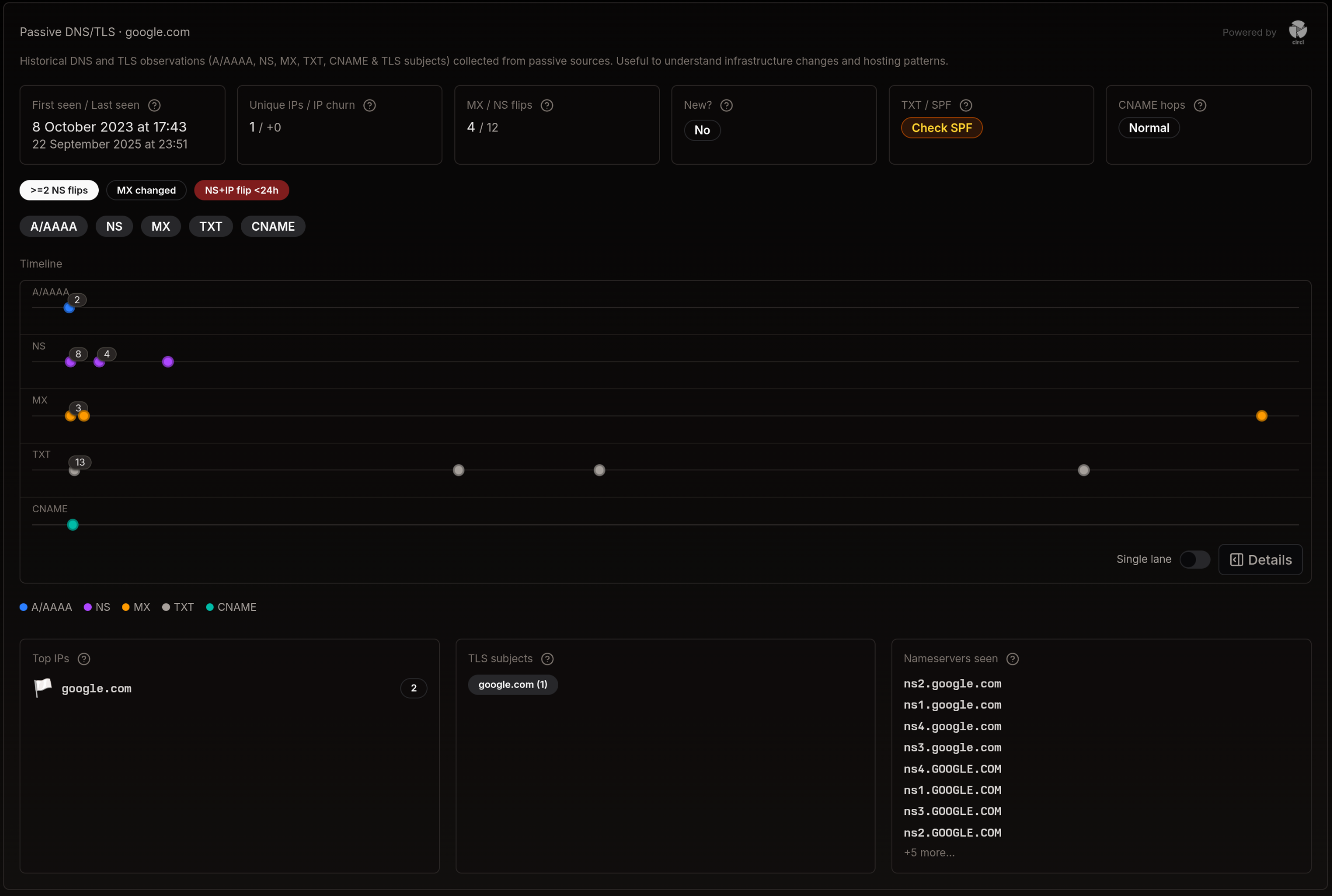
Reading the Panel
Section titled “Reading the Panel”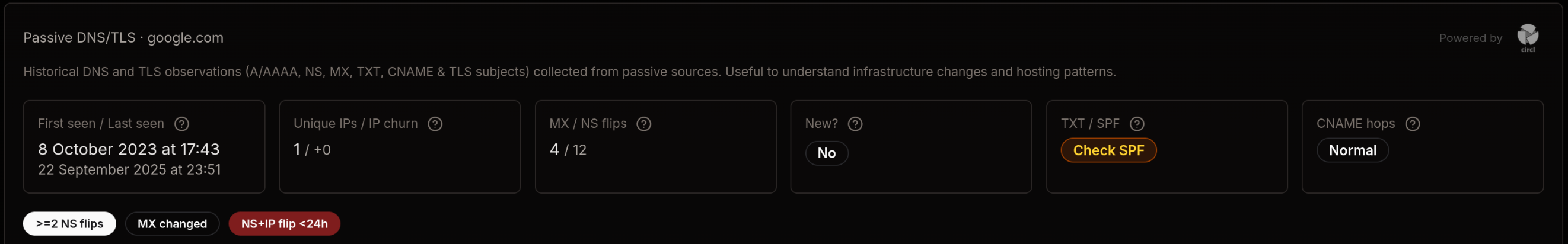
- KPIs: First/last seen, IP churn, MX/NS flips, TXT/SPF health, CNAME hops
- Filters: Toggle record types (A/AAAA, NS, MX, TXT, CNAME)
- Timeline: Historical observations grouped by record type
- Legends & details: Hover to see timestamps and counts; switch single-lane for compact view
- Context cards: Top IPs, TLS subjects, and nameservers seen
Timeline view
Section titled “Timeline view”The timeline condenses all observed DNS changes into a single visual so you can quickly spot bursts, gaps, and pivots in infrastructure. Use it to correlate record flips with registration events, hosting moves, or certificate subject shifts.

- Filter: Toggle A/AAAA, NS, MX, TXT, CNAME to focus the series
- Details: Hover points to see timestamp and count
- Compact: Use single‑lane for a compressed timeline
Workflow Tips
Section titled “Workflow Tips”1. Track hosting changes
Section titled “1. Track hosting changes”- Filter to A/AAAA and review points on the timeline
- Compare with TLS subjects to see certificate continuity across hosting moves
2. Investigate mail infrastructure
Section titled “2. Investigate mail infrastructure”- Enable MX and TXT to validate SPF/DKIM posture changes
- Multiple MX flips in short time windows can indicate staging or abuse
3. Map nameserver relationships
Section titled “3. Map nameserver relationships”- Enable NS and review churn
- Cross-reference with other suspicious permutations to find shared providers
Correlating Results
Section titled “Correlating Results”- In lookup results, Passive DNS/TLS augments each permutation’s context
- In the Rules Engine, combine passive signals with infrastructure and registration data to raise confidence
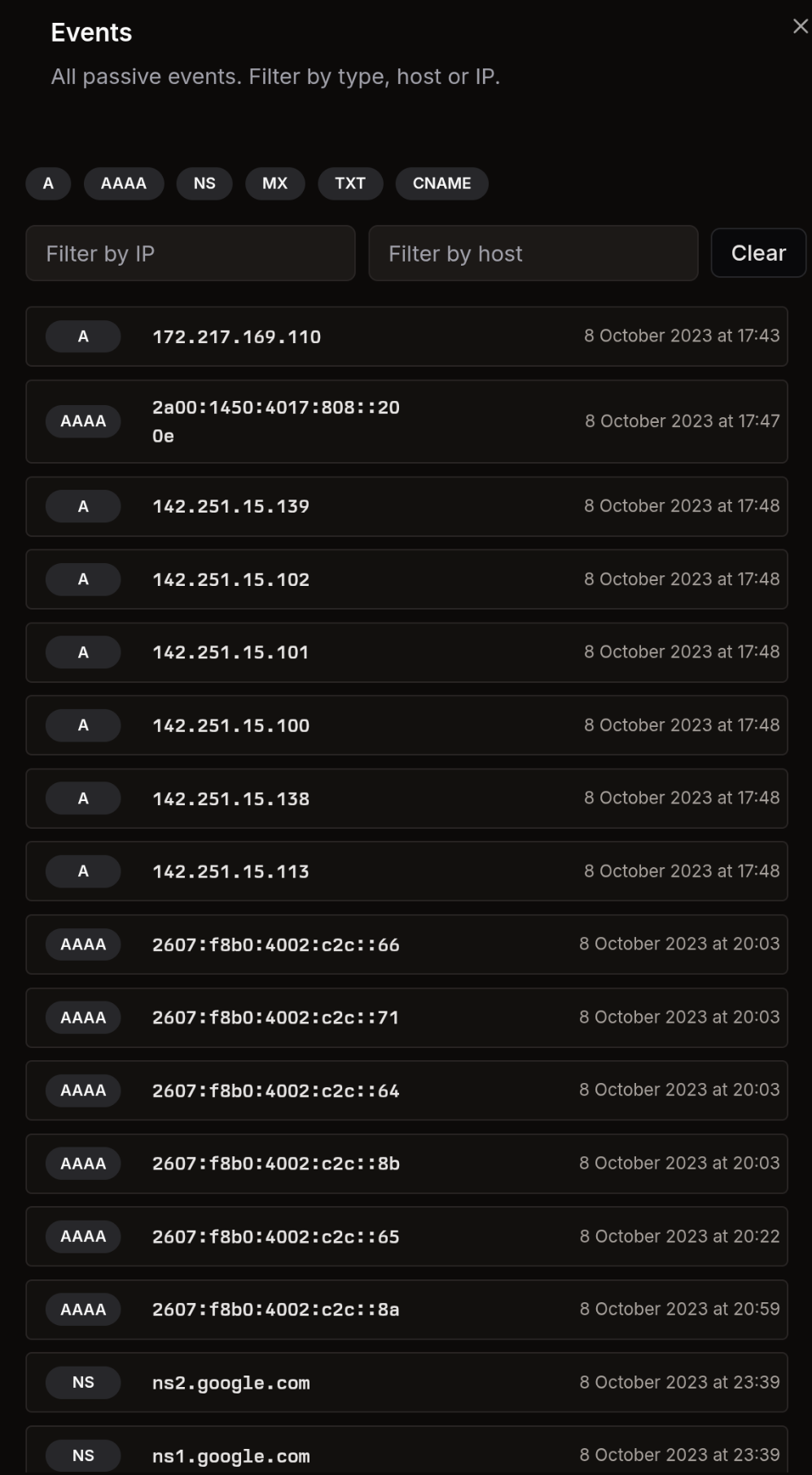
Events View
Section titled “Events View”Open the detailed events view to browse all passive observations.
- Type filters: Quickly scope to A, AAAA, NS, MX, TXT, or CNAME
- Filter by IP / host: Free-text filters to narrow results
- Chronological list: Each row shows the record, value, and timestamp
- Clear: Resets all filters
Use this view to audit exact changes and pivot into specific infrastructure items.
API Context (Optional)
Section titled “API Context (Optional)”When streaming results from the API, Passive DNS/TLS events appear as operations:
{"op":"PassiveDns","data":[{"rrtype":"NS","rrname":"ns1.example.com","rdata":"example.com","time_first":1751627704,"time_last":1751627704,"count":1}]}See the API guide for general streaming patterns: API Integration Guide.
Best Practices
Section titled “Best Practices”- Use the single-lane toggle for compact investigations in wide tables
- Focus on bursts of change (e.g., multiple NS/MX flips) as triage signals
- Pair passive data with classification and whois/rdap to strengthen confidence