Rules Engine Guide
The Rules Engine is the heart of Have I Been Squatted’s threat detection system. It allows you to create sophisticated detection patterns that identify potentially malicious domain permutations based on various indicators and heuristics.
Understanding Rules
Section titled “Understanding Rules”Rules are detection patterns that define what constitutes suspicious domain activity. Each rule combines multiple conditions and assigns threat likelihood scores across different categories to help you identify potential threats automatically.
What Rules Detect
Section titled “What Rules Detect”Rules can identify suspicious domains based on:
- Infrastructure indicators: Hosting providers, geographic locations, ASN patterns
- DNS patterns: Suspicious nameservers, MX records, resolution behavior
- Registration data: Creation dates, registrar patterns, WHOIS information
- Technology fingerprints: Web technologies, certificates, hosting stacks
- Behavioral patterns: Traffic patterns, content analysis, domain relationships
Rule Classification System
Section titled “Rule Classification System”Severity Levels
Section titled “Severity Levels”| Level | Description | Use Case |
|---|---|---|
| critical | Highest severity, immediate attention required | Active threats, confirmed malicious activity |
| high | High severity, requires timely investigation | Likely threats, suspicious patterns |
| medium | Medium severity, investigate as appropriate | Potentially suspicious activity |
| low | Low severity, potentially interesting event | Unusual but not necessarily harmful |
| informational | Informational event, no action needed | Baseline activity, monitoring |
Rule Status
Section titled “Rule Status”| Status | Description | Reliability |
|---|---|---|
| stable | Well-tested and reliable rule | Production-ready |
| test | Rule under testing, might produce false positives | Use with caution |
| experimental | Rule in early development, likely unstable | Development only |
| deprecated | Rule no longer recommended for use | Disable or replace |
| unsupported | Rule is not maintained or supported | Avoid usage |
Threat Scoring System
Section titled “Threat Scoring System”Each rule assigns likelihood scores (0-100%) across three threat categories to help prioritize responses:
Scoring Categories
Section titled “Scoring Categories”- Malware: Likelihood the domain hosts or distributes malware
- Phishing: Likelihood the domain is used for credential theft
- Impersonation: Likelihood the domain impersonates a legitimate brand
Query Language
Section titled “Query Language”Rules are written using the Upsilon query language, a Lucene-like syntax that’s powerful yet easy to learn. For complete syntax documentation, see the Upsilon Query Syntax Reference.
Quick Example
Section titled “Quick Example”# Detect recently registered domains with high phishing scoresregistration_metadata.registration_date.days_since:<=30 ANDclassification.phishing:>0.8Creating Custom Rules
Section titled “Creating Custom Rules”Getting Started
Section titled “Getting Started”Navigate to Monitoring → Rules in your dashboard and click Create Rule to open the rule builder. The creation process is divided into three simple steps:
Step 1: Basic Information
Section titled “Step 1: Basic Information”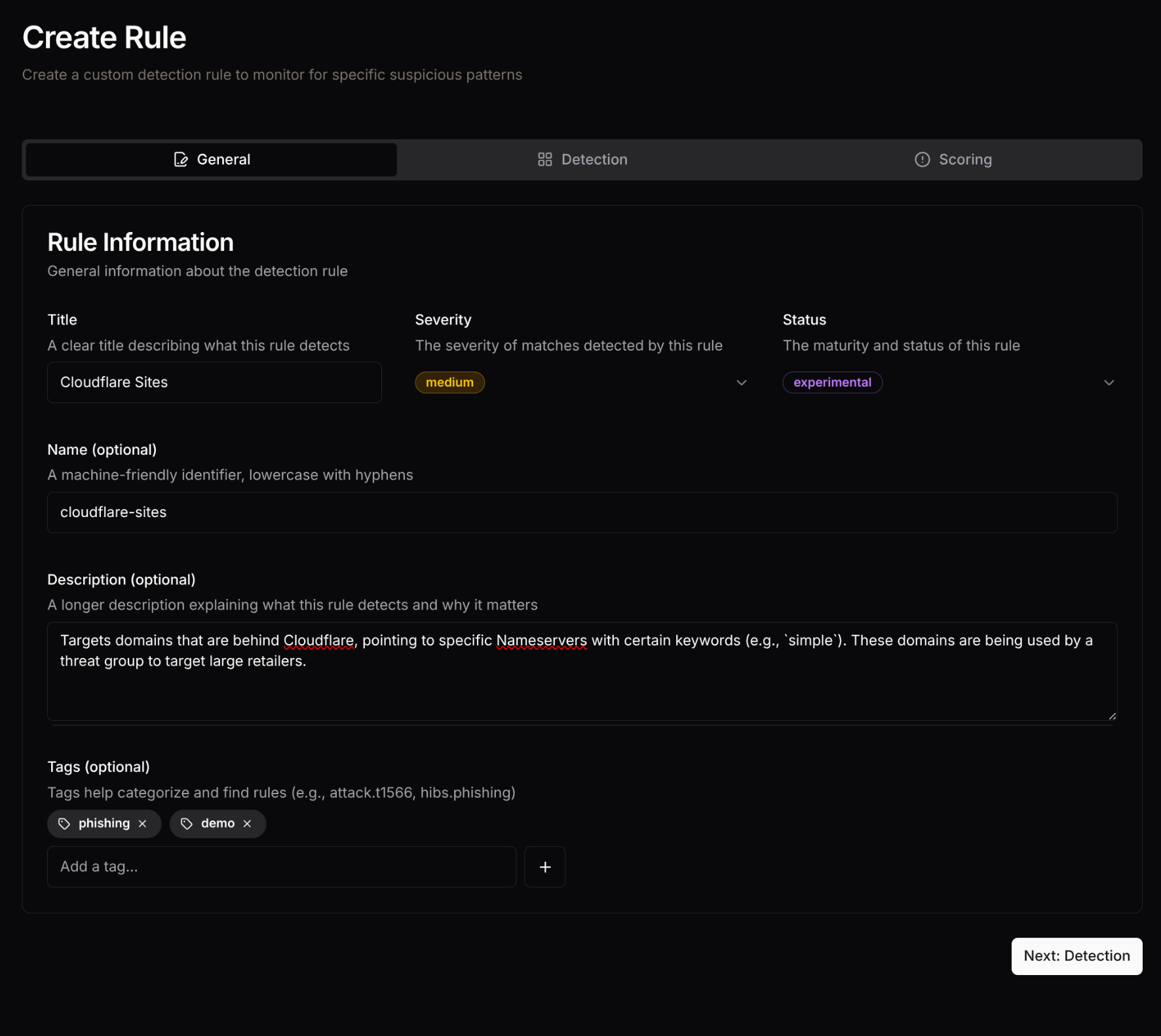
In the first step, provide the fundamental details for your rule:
- Title: A clear, descriptive name for your rule
- Description: Detailed explanation of what the rule detects
- Tags: Categorization labels for organization and filtering
- Level: Choose the appropriate severity level based on the threat
- Status: Set the maturity level (start with
testfor new rules)
Step 2: Detection Logic
Section titled “Step 2: Detection Logic”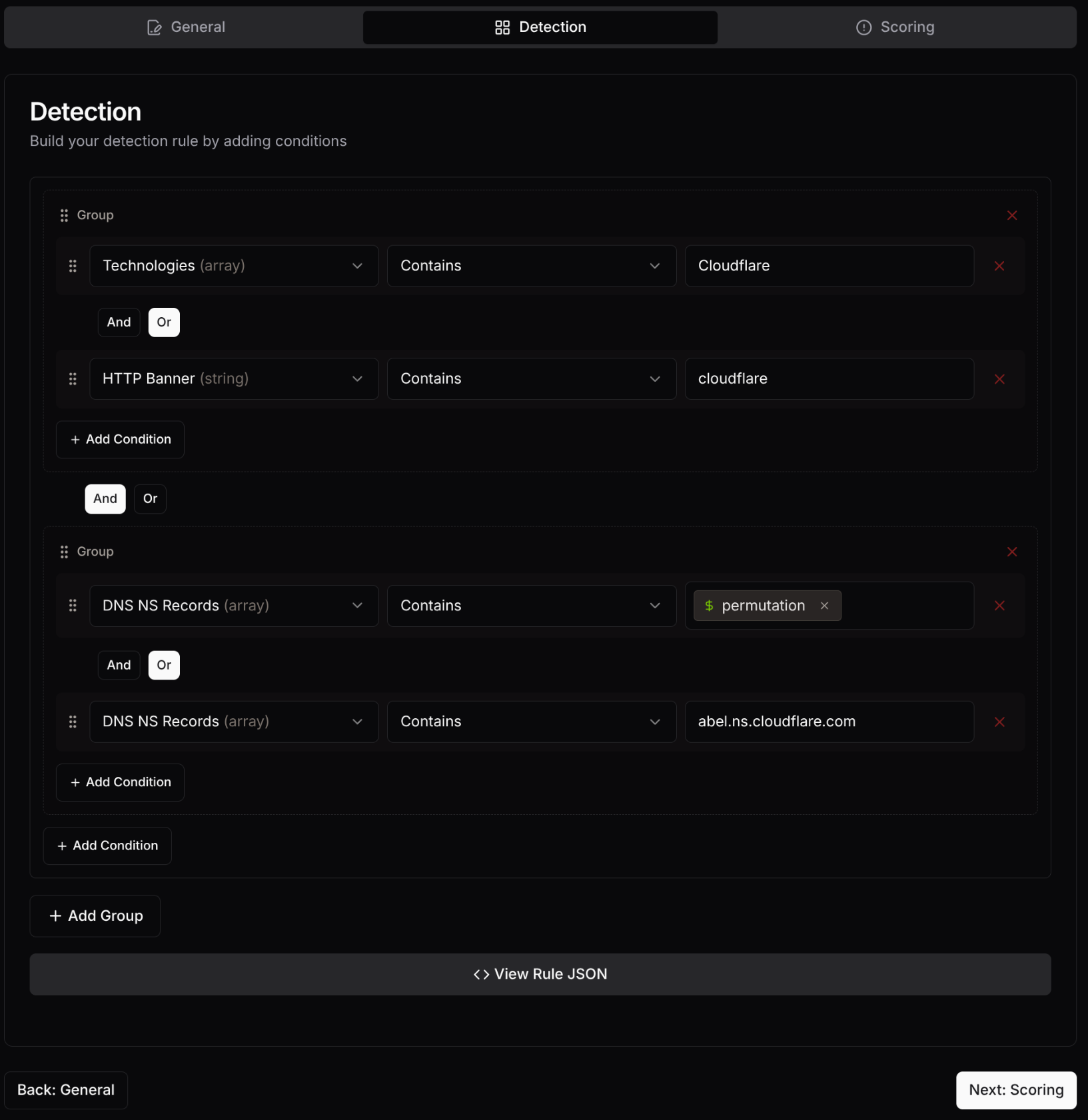
This is where you define the conditions that will trigger your rule. The visual detection builder allows you to:
Common Detection Patterns
Section titled “Common Detection Patterns”Infrastructure-Based Detection
- ASN numbers associated with malicious hosting (
geolocation.asn.number) - Geographic locations with high threat activity (
geolocation.country) - Suspicious hosting providers or data centers (
geolocation.asn.name)
Technology-Based Detection
- Specific web technology combinations (
technologies) - Certificate authorities or SSL configurations (
origin_x509.issuer) - Content delivery networks and hosting stacks (
http_banner)
Registration-Based Detection
- Recently registered domains (
registration_metadata.registration_date) - Suspicious registrars or registration patterns (
registration_metadata.registrar) - WHOIS data anomalies and patterns (
whois)
DNS-Based Detection
- Nameserver patterns indicating malicious hosting (
dns_ns) - MX record configurations (
dns_mx) - DNS resolution behavior and patterns (
dns_a,dns_aaaa)
Classification-Based Detection
- Machine learning confidence scores (
classification.phishing,classification.legitimate) - Domain similarity metrics (
levenshtein_distance) - Domain age and temporal patterns (
created_on)
Building Conditions
Section titled “Building Conditions”Use the visual builder to create detection logic by:
- Adding Selections: Define groups of conditions that check specific fields
- Setting Values: Specify what values to match against
- Combining Logic: Use AND/OR operators to combine multiple conditions
Step 3: Threat Scoring
Section titled “Step 3: Threat Scoring”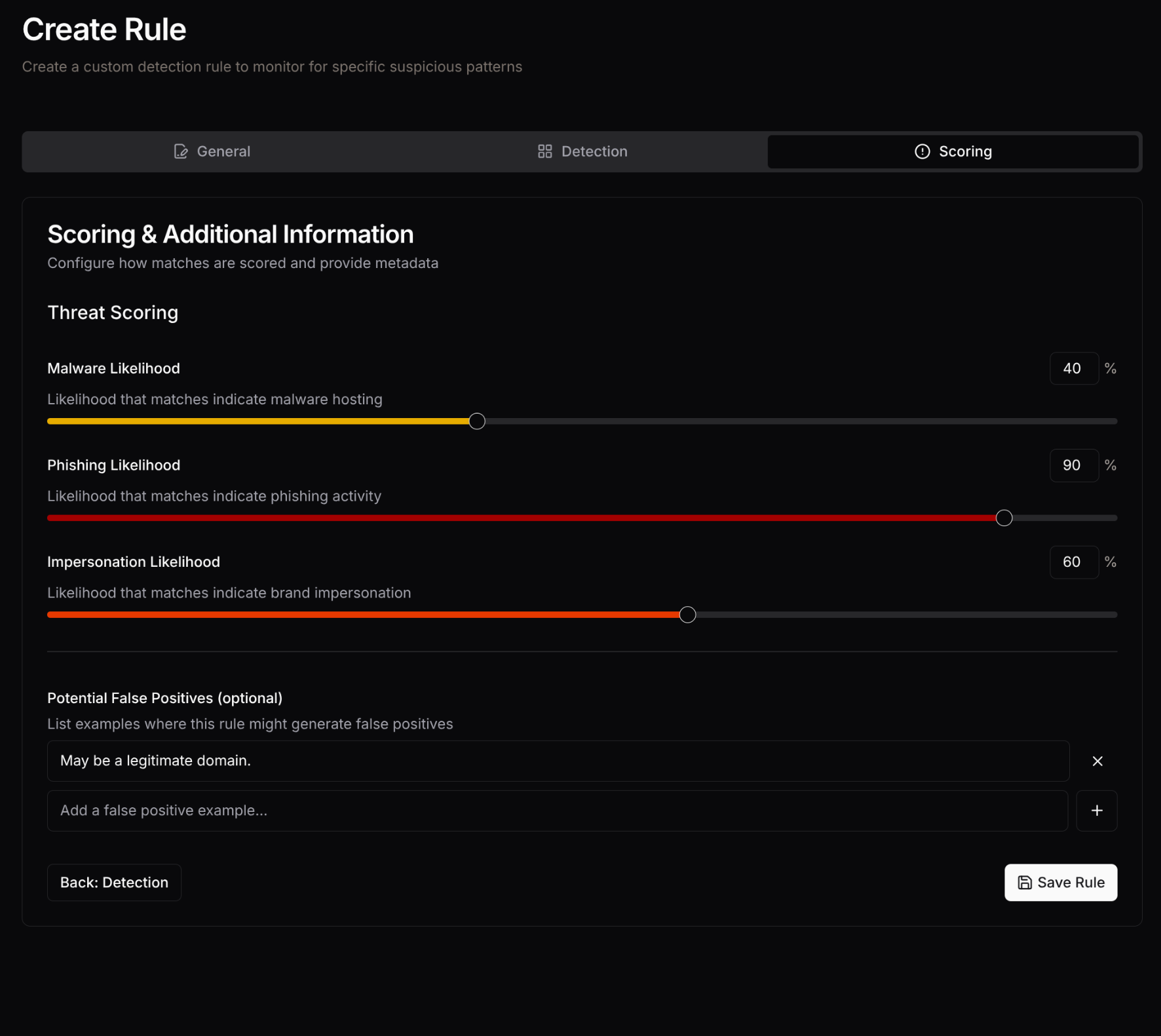
In the final step, configure the threat likelihood scores for each category:
- Malware Score (0-100%): How likely is this domain to host malware?
- Phishing Score (0-100%): How likely is this domain used for phishing?
- Impersonation Score (0-100%): How likely is this domain impersonating a brand?
Scoring Guidelines
Section titled “Scoring Guidelines”- 80-100%: High confidence threat indicators
- 60-79%: Moderate confidence, requires investigation
- 40-59%: Low to moderate suspicion
- 20-39%: Minimal threat likelihood
- 0-19%: Very low or informational only
Managing Existing Rules
Section titled “Managing Existing Rules”Global vs User Rules
Section titled “Global vs User Rules”- Global Rules: Provided by our security team, cannot be modified or disabled
- User Rules: Custom rules you create, fully editable and manageable
Rule Actions
Section titled “Rule Actions”- Enable/Disable: Control whether user rules are active in your monitoring
- Edit: Modify user-created rules to improve performance or reduce false positives
- Delete: Remove user-created rules that are no longer needed
- View Details: See rule logic, scoring, and recent alerts
Best Practices
Section titled “Best Practices”Rule Design Principles
Section titled “Rule Design Principles”- Start Simple: Begin with basic conditions and add complexity gradually
- Test Thoroughly: Use sample data to validate rule behavior before deployment
- Document Clearly: Provide detailed descriptions explaining the rule’s purpose
- Tag Consistently: Use standardized tags for better organization
Avoiding False Positives
Section titled “Avoiding False Positives”- Be Specific: Use precise conditions rather than broad pattern matching
- Add Exclusions: Account for legitimate use cases that might trigger the rule
- Monitor Performance: Regularly review alerts to identify false positive patterns
- Iterate and Improve: Refine rules based on real-world feedback
Common Use Cases
Section titled “Common Use Cases”Infrastructure Monitoring
Section titled “Infrastructure Monitoring”Suspicious Hosting Providers
# Flag domains on known malicious ASNsgeolocation.asn.number:[16509 13335] ANDclassification.phishing:>0.5Geographic Anomalies
# Detect domains hosted outside expected regionsNOT geolocation.country:[US CA GB] ANDlevenshtein_distance:<5Behavioral Detection
Section titled “Behavioral Detection”Registration Patterns
# Examples:# - Registered more than 90 days ago: registration_metadata.registration_date.days_since:>90# - Registered within last 30 days: registration_metadata.registration_date.days_since:<=30# - Expires in more than 1 year: registration_metadata.expiration_date.days_until:>365registration_metadata.registration_date.days_since:>90 ANDregistration_metadata.registrar:*suspicious*Technology Fingerprinting
# Flag domains using suspicious tech stackstechnologies:@*PhishingKit* ORhttp_banner:*nginx/0.8.5*Rule Categories & Tagging
Section titled “Rule Categories & Tagging”Recommended Tag Structure
Section titled “Recommended Tag Structure”Use consistent tagging for better organization:
- Category Tags:
infrastructure,behavioral,technology,registration - Threat Type:
phishing,malware,impersonation,spam - Confidence:
high-confidence,medium-confidence,low-confidence - MITRE ATT&CK:
attack.initial_access,attack.t1566(where applicable)
Standard Categories
Section titled “Standard Categories”hibs.infrastructure- Infrastructure-based detectionhibs.phishing- Phishing-specific patternshibs.malware- Malware-related indicatorshibs.campaign- Campaign-specific detectionhibs.experimental- Experimental/testing rules
Troubleshooting
Section titled “Troubleshooting”Common Issues
Section titled “Common Issues”Rule Not Triggering
- Verify rule is enabled and has appropriate status
- Check that field names match available data
- Review condition logic for errors
- Test with known positive samples
Too Many False Positives
- Refine selection criteria to be more specific
- Add exclusion conditions for legitimate cases
- Lower severity level or adjust scoring
- Review and update rule description/tags
Query Language & Field Reference
Section titled “Query Language & Field Reference”The Rules Engine uses the Upsilon query language for writing detection rules. For detailed information:
- Query Syntax: See the Upsilon Query Syntax Reference for operators, examples, and best practices
- Available Fields: Check the Signals Reference for all available fields and their types
Getting Help
Section titled “Getting Help”For comprehensive rule creation assistance:
- Query Language: Learn the Upsilon syntax and operators
- Field Reference: Browse all available signals and fields
- Examples: Review the rule patterns and examples throughout this guide
- Support: Contact our security team at hello@haveibeensquatted.com for advanced rule optimization